In today’s digital age, it’s nearly impossible to not hear about the constant attacks that computer systems face each and every day. Only last May did we see news about several businesses which include the NHS being hit by cyber attacks on a huge scale. So it’s no wonder that in this day and age, people need to be prepared and ready to defend themselves against potential malicious attacks that can happen to anyone if you’re unlucky enough.
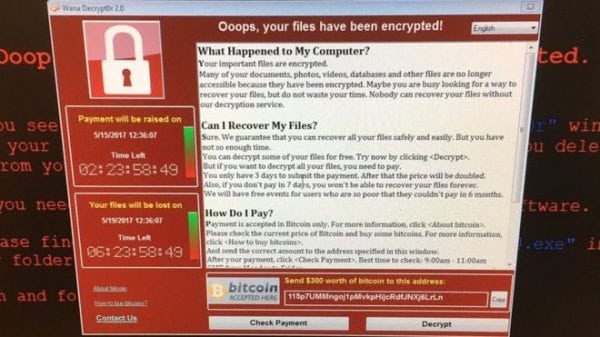
Our Systems Administrator, James Dyer explored what would happen if our own computer systems were attacked by what’s known as a ‘phishing attack’. Whilst in our ‘dummy’ attack, only two people fell victim which is still more than enough people, other organisations that are much, much bigger have an even trickier problem keeping their users safe. The attack that hit the NHS was due to a malicious computer program, called ‘ransomware’ which encrypts files and demands payment before the files can be accessed again.
How do you stay safe?
Unfortunately there isn’t one right answer for everyone, but there are some good tips that can help you reduce how susceptible you are to cyber attacks. These are very simple methods of staying safe and can be applied to home computers as much as work computers.
- Don’t open emails from people you’ve never spoken to before that have suspicious email addresses. Don’t just look at the sender’s name, check the sender’s email address as well.
- Be vigilant about message contents. Is it something you’d expect to receive from the sender? There have been many attacks which exploit a users mail client, and then send from that person to everyone in the address book.
- If you weren’t expecting to receive an attachment in an email, don’t open it or forward it on to anyone unless instructed to (like a systems administrator for example).
- Avoid clicking on strange links in emails or messenger apps.
- Perform regular virus checks on your computer.
- Always make sure that you have the most up-to-date software available to make sure you are protected against known vulnerabilities.

Why should I update?
Like many things nowadays, such as the iPhone with regular software updates – people get in the habit of updating to the latest and greatest but some people get anxious. Sometimes updates don’t always go to plan and can introduce new issues (what’s known in software as ‘a bug’). Bugs are generally classified on a scale from ‘Trivial’ to ‘Blocker’ where trivial is a very minor, and not particularly important issue that may or may not warrant a fix any time soon. A blocker on the other hand is a very serious and business critical problem. It’s something that needs an update to fix it as soon as possible because it potentially causes a serious security breach in the software.
Over a software’s lifetime, you can expect to hear about at least one problem that can be classed as a blocker. Nothing is ever one hundred percent perfect, so there is always that risk with literally everything digital. As a general rule of thumb, it’s good to wait before updating anything for at least a day or two unless a security vulnerability has been fixed in case it introduces new problems. This gives you some time to see how other people are getting on with the new version before you decide to take the leap of faith and update. This should of course be taken on a case by case basis, but it can save you from new issues that are introduced.
How do you hack something?
There are online courses that you can take (some free and others that come with a price) where you can learn how to hack something and understand how you can protect yourself from such attacks. Hacking can be both easy and difficult and is not always as cool as it’s made to look in films! It’s not always a wall of green numbers going up and down a screen of course!

It’s important to never give someone information unless it’s coming from a verified source. A good example is your bank, which will be able to see your account number, address and potentially even answers to your security questions. They won’t need to phone or email you asking for these details. They’ll also probably have a system in place where they can access a restricted version of your account when they need to, so they’ll never need your password either. If someone asks for this kind of information from you, they’re more than likely phishing you.
How do you report bugs?
It may not occur to you, but in reality everyone is a quality assurance tester of computer systems. Not just on a software level but hardware too. It depends on the vendor as to how you can report problems to them. Some companies or organisations will have their own systems in place internally to record problems and fix them. If you’re willing to help fight for a good cause, you can also hack for good. There are bug bounty programs available which let people hack responsible in return for cash or ‘swag’ rewards.

What should you do now?
Make sure your software is updated to the latest versions and keep your passwords strong and secure. You can do this by ensuring each account you have online has a unique password with letters, numbers and symbols. A good length is usually around the ten to twenty character mark. You should also make sure that you filter any spam emails you receive and also check that the people you are talking to and sharing information with are who they say they are.
How do you keep yourself safe online? What tips and tricks do you try and stick to when you use the internet? Share your useful tips and spread any handy information to make sure your friends and family are on top of their security, especially elderly people who might be unaware of these things. It can seem like a lot of effort, but it is worth it!